LDAP Client
LDAP task is used to communicate with LDAP server and provides three functions ??? list/update/authenticate. List and update are for general purpose but authentication is only for user information. Because LDAP is mostly used for the authentication of users.
Input
Use SSL?
Secure communication with LDAP
Default value is no.
If SSL is enabled, ldaps:// is used.
SSL Factory
Custom SSL socket factory class
It is required when the communication with LDAP need to be secure but the certificate of the LDAP server is not valid
Host Name
LDAP Host
If SSL is enabled, use DNS name instead of ip address.
Port
LDAP Port
Default port for LDAP is 389 and 636 for LDAPS.
Base DN
Base DN for the connection
Base DN is the entry point to perform further operation.
ex) DC=active,DC=myldap,DC=com
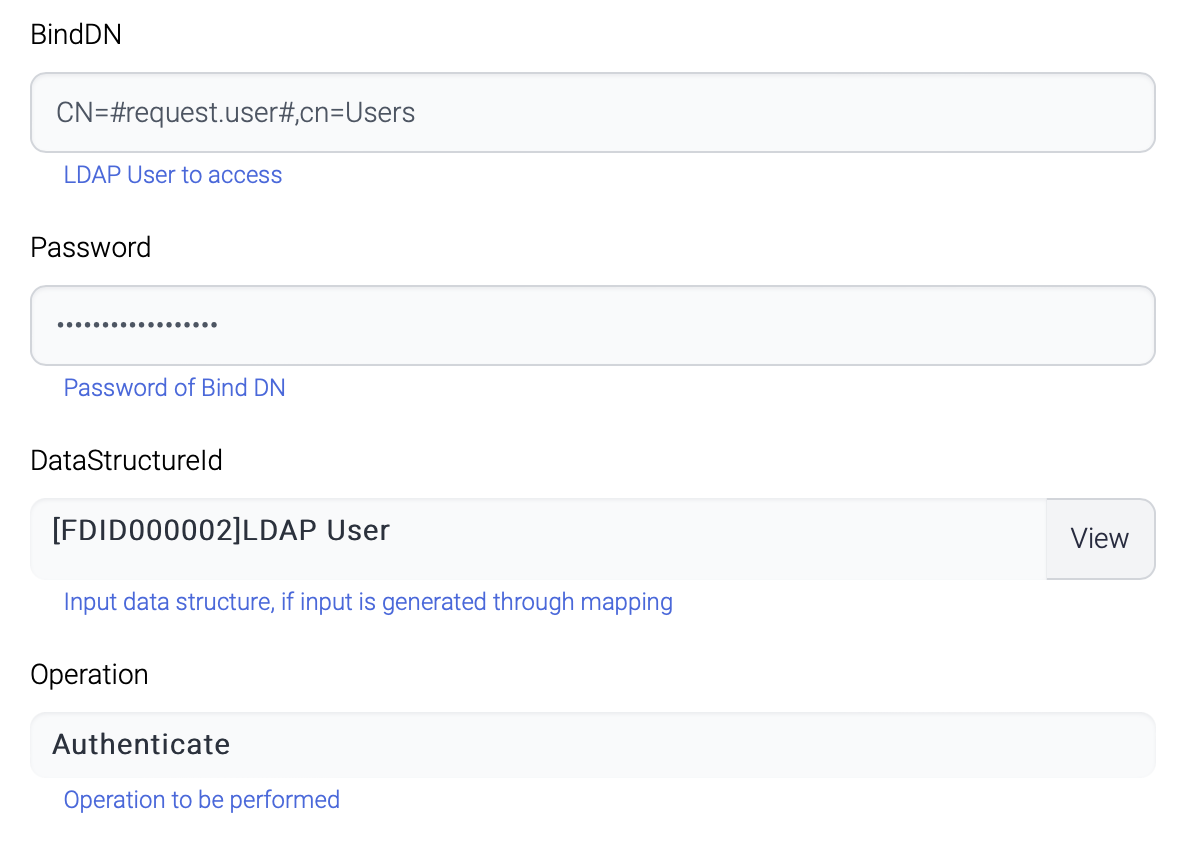
Bind DN
User entry to access the target LDAP
Bind DN starts after the Base DN
ex)CN=Chris,CN=Users means CN=Chris,CN=Users, DC=active,DC=myldap,DC=com
Password
Password of BindDN
DataStructure Id
Data structure id for update operation
This id is used to generate input data through mapping
Input
Input parameter or data
If input data is generated through mapping or other data from previous tasks, use ## encloser.
ex)#MappingResult#
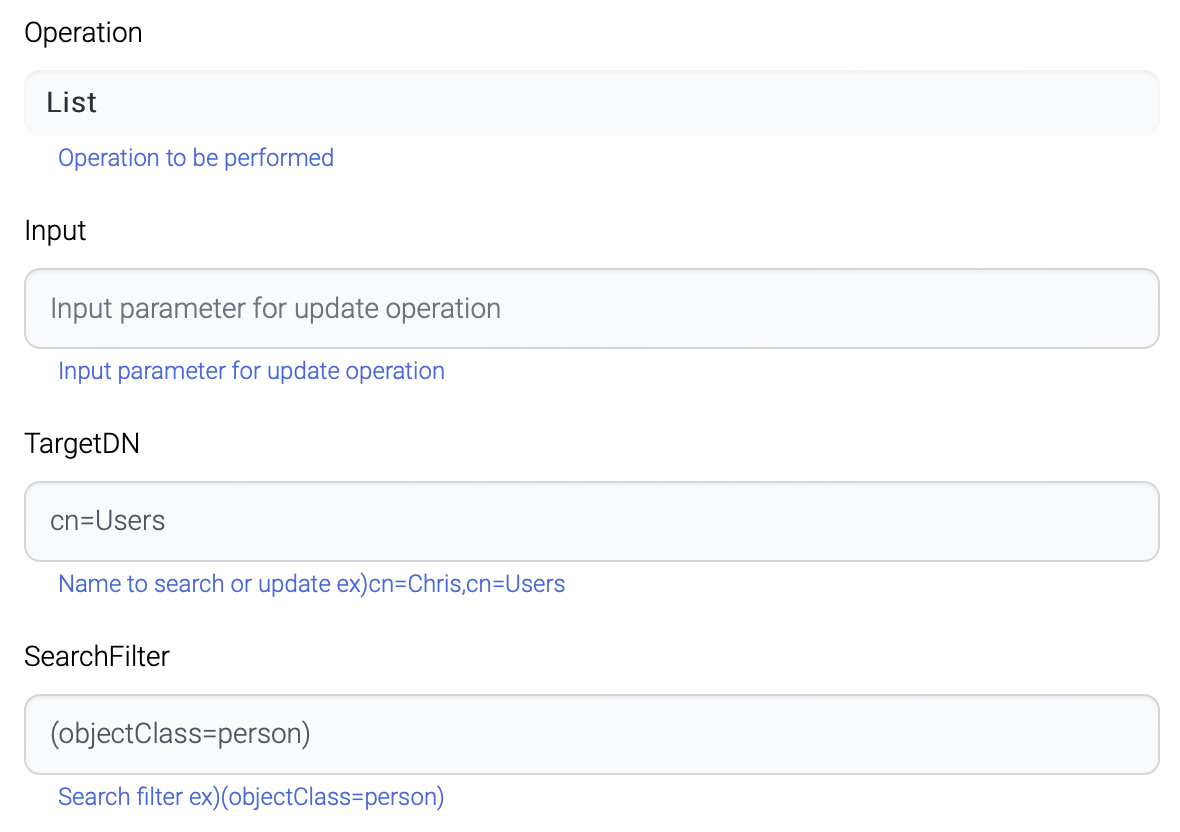
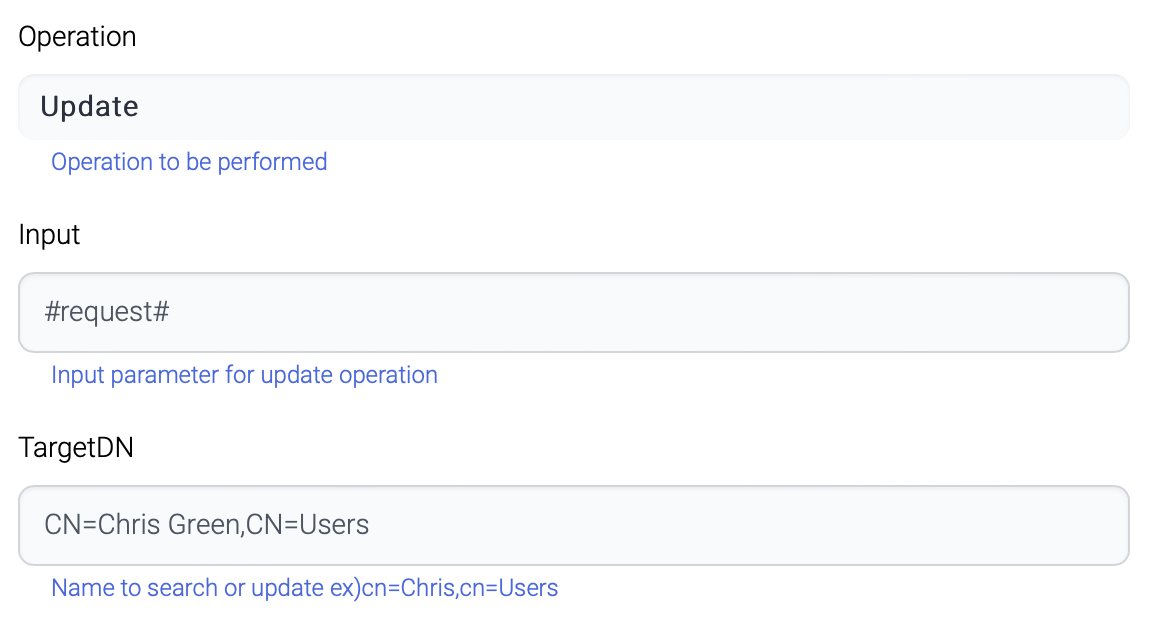
Target DN
Name to search or update
For update, this TargetDN is the target entry to be updated.
ex) CN=Chris,CN=Users
For list, this TargetDN is the parent DN where the search is started.
ex) CN=Users
Search Filter
Search filter.
Each filter consists of (attributename=attributevalue).
Use Data Structure?
Used to map the result of the list to the specific data structure.
Output
Output properties are the result of a task execution and assigned by the task.
Tasks with same type generates same result parameters. If a task is used more than once, the result data of the previously executed task will be overwritten by latter task.
You need to assign different names to avoid duplication.
ResultCount
List count
ResultRecord
The result of list operation
DataStructureId
Data structure id which will be used in mapping, if mapping exists.
Example
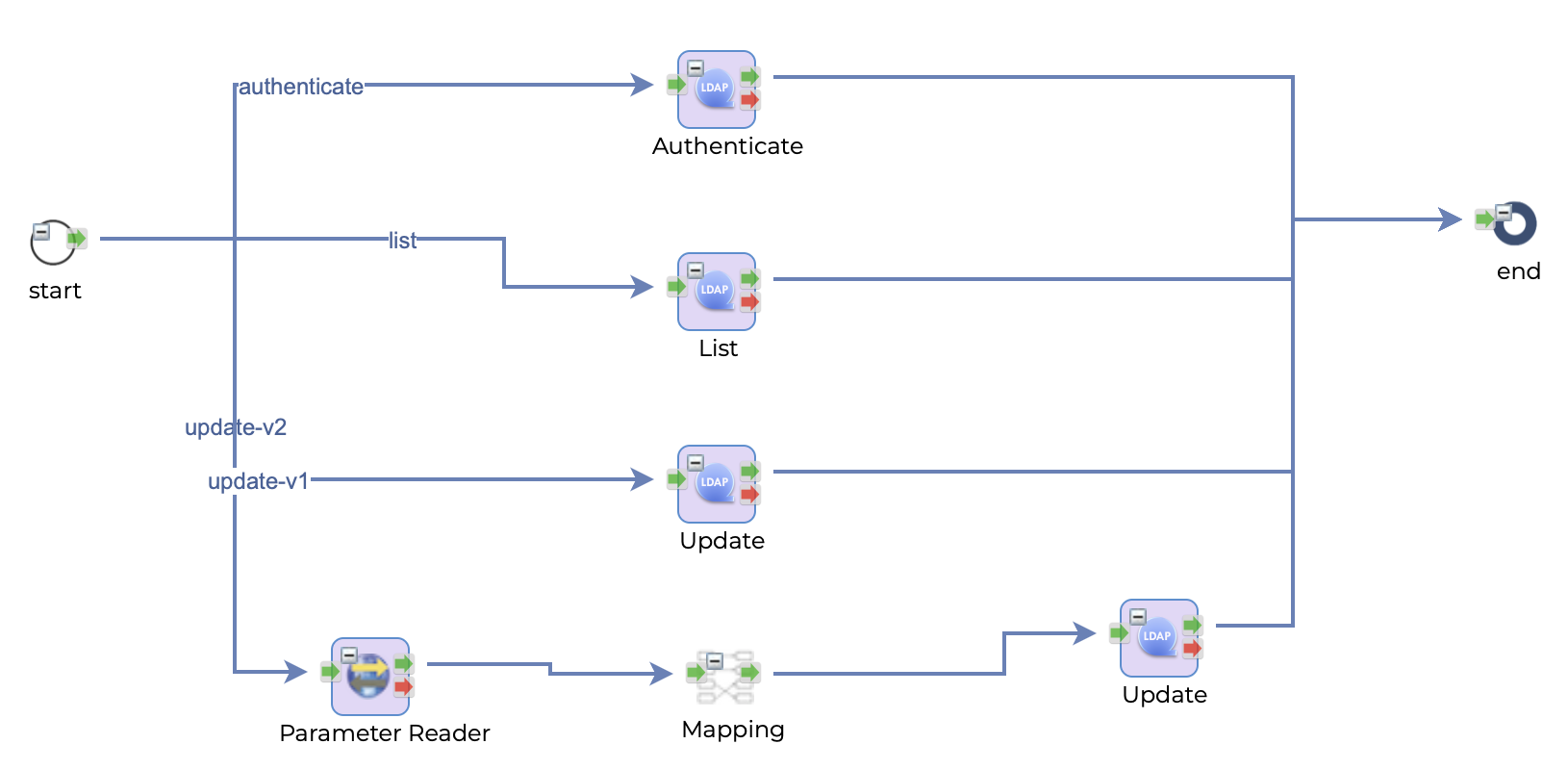
Authenticate
BindDN is the user who will be authenticated.
List
List operation requires TargetDN and Search Filter
Update
Input of Update operation can be acquired through mapping or from output of previous components.
Sample REST request
URL : http://localhost:8080/ api/ LDAPTest01/v1?__RoutingPath=update-v1
(*) __RoutingPath: list, authenticate, update-v1, update-v2
Request Header
Content-Type: application/json
X-Api-Key: 813ffe59f7ad9350
Request Body
Custom SSL Socket factory.
To use custom SSL socket factory, you have to implement your own SSLSocketFactory. Most of the reason you need a custom factory is the target LDAP server does not have valid certificate. The default java SSL implementation does not allow invalid certificate or incorrect host name/ip address which does not match the certificate. In that case, we need to avoid that limitation. The main purpose of the custom SSL socket factory is to make the target LDAP valid host.
There are three steps to make the invalid target LDAP valid.
· Implement custom SSL Socket Factory.
· Register host name and address to /etc/hosts file
· Register custom SSL socket factory to ISM.
You will implement a TrustManager which returns valid result for your target server in your SSLSocketFactory..
If no error is thrown from checkClientTrusted() and checkServerTruster(), JVM security manager treats the target host is valid.
Deployment of custom SSL socket factory
Create a new module directory under wildfly-10.1.0.Final/modules/system/layers/base/com/ism/
$>mkdir -p ldap/main
Put your ssl factory implementation under main directory.
Create a file named module.xml under ldap/main directory and add these contents.
(*) This sample implementation uses slf4j, so slf4j dependency is added.
com.ism.ldap means the directory
Restart wildfly.
Last updated