System
System manages system information of these types. These systems are published to the runtime and loaded into memory before being used for incoming transactions.
Database
(s)FTP
Http(s)
Socket
SMTP
IBM MQ
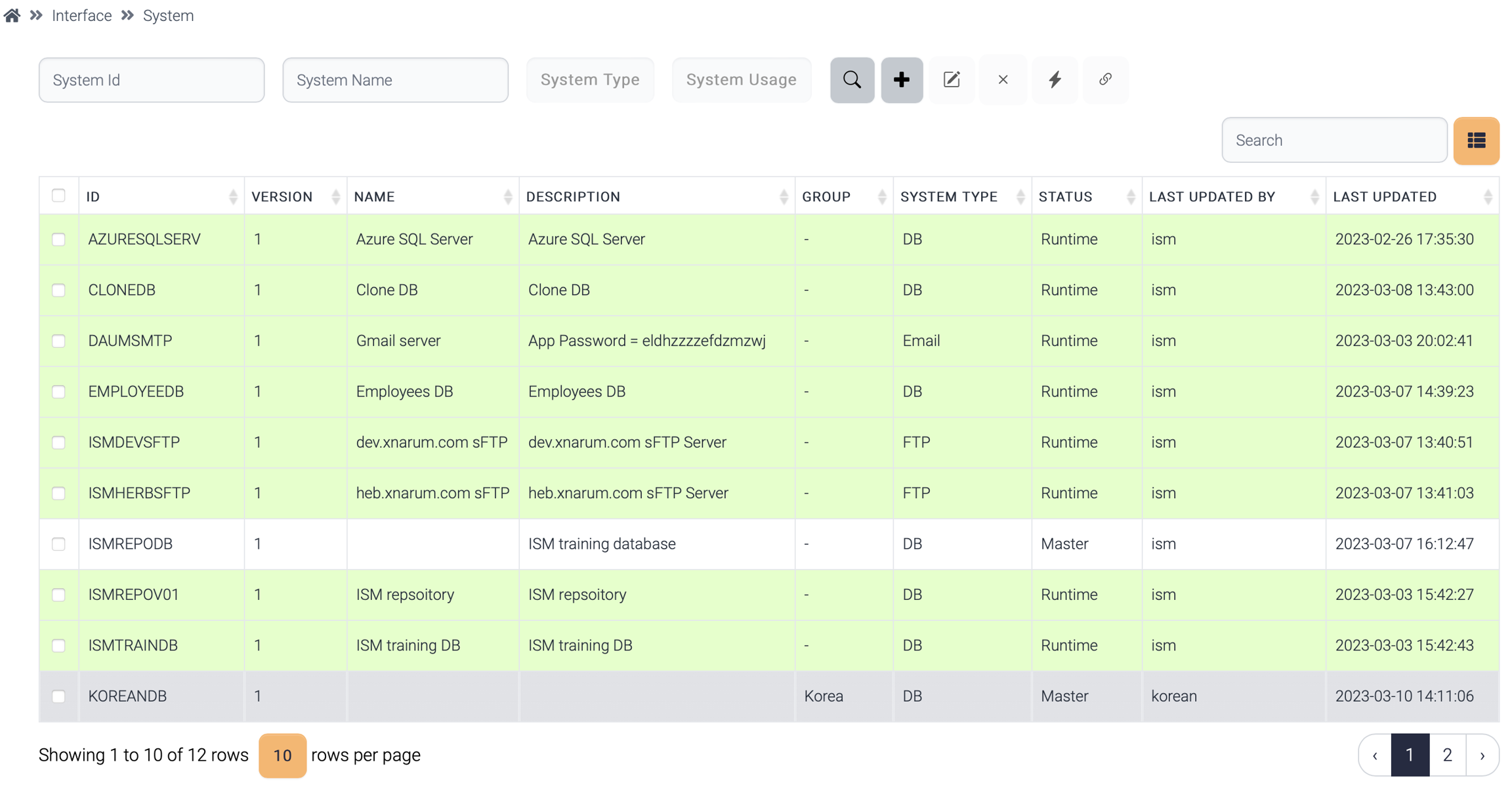
The systems created by a normal user of a group belongs to the group. And other users of different groups cannot see the systems. But the admin user can see all the systems.
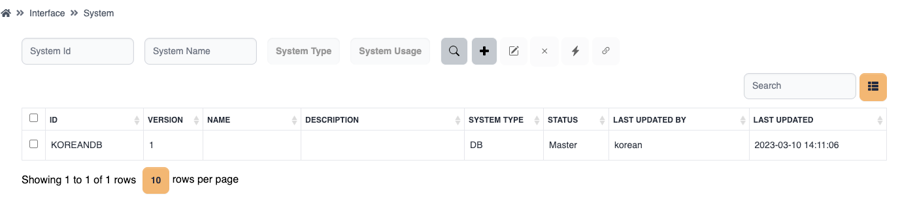
Available operations
These operations are common for system, data structure, field group, field.
Publish ( )
)
System information is loaded from database, converted into an object, and saved into a memory cache. If the system is used by the running instances, the object is replaced with the new one.
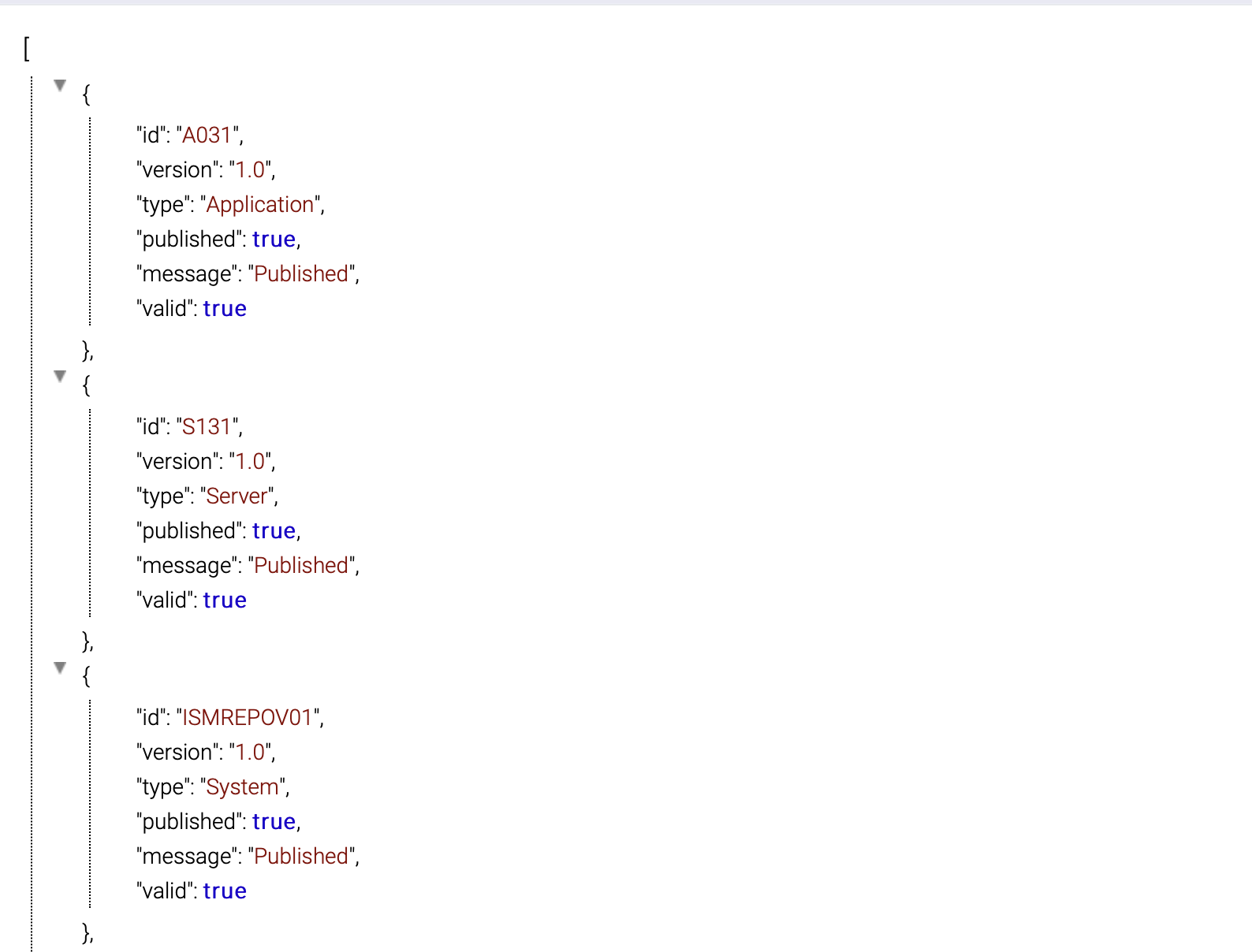
When a system is published, if that system has sub items, all the sub items are published together.
Reference ( )
)
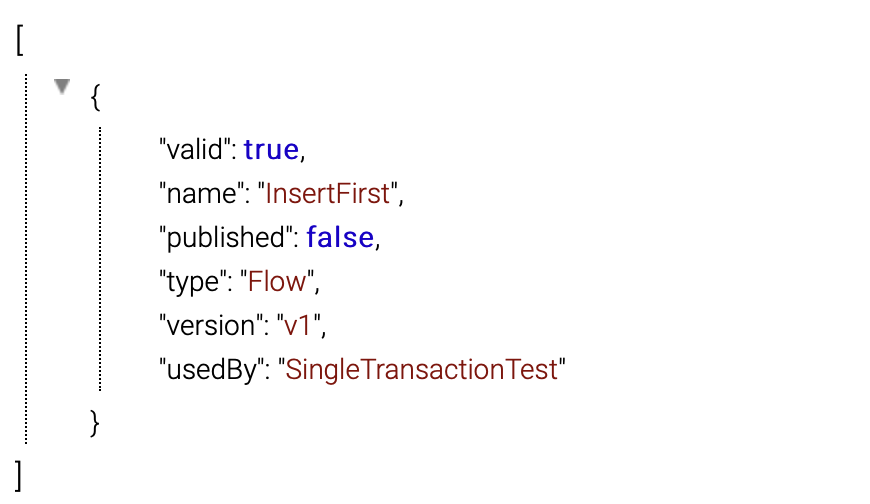
If a system is used by any flow, this system is displayed in green background.
The hierarchies of the items are these.
· Flow > system
· Flow > data structure > field group > field
Database
Database manages these properties.
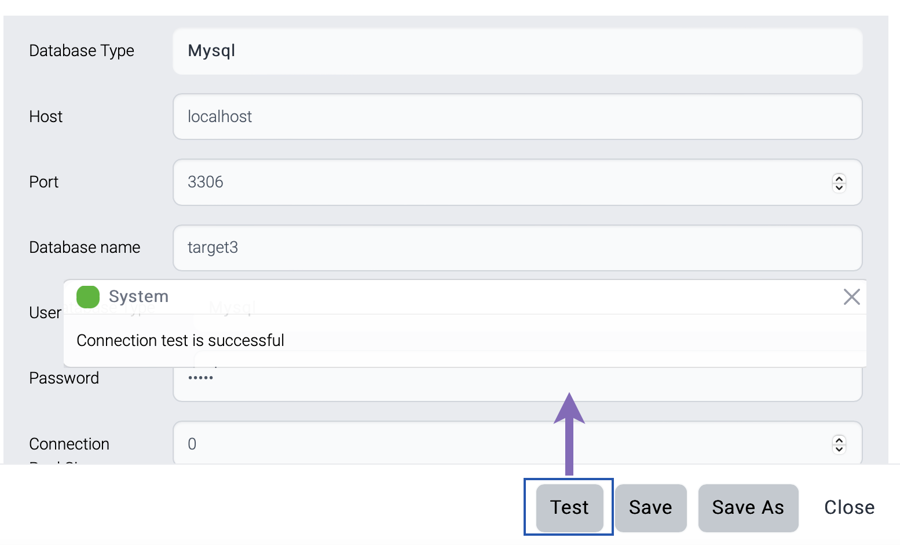
Database Type
Database type
Host
Database host
Port
Database port
Database name
Database name
User
Database user
Password
User password
Connection Pool Size
Connection pool size. Default size is 10
Driver class
If database type is not listed in ISM, custom driver class can be set
Driver URL
Driver class url - file:///jdbc_driver_path/jdbc_driver_jar_file
Validation Query
Validation for the connection. Ex) select 1
Connection String
JDBC connection String. Refer to Help
· Connection String
mysql
jdbc:mysql://localhost:3306/database_name
oracle
jdbc:oracle:thin:@localhost:1521/service_name
jdbc:oracle:thin:@localhost:1521:SID
Sqlserver
jdbc:sqlserver://localhost:1433;databaseName=database_name
Postgresql
jdbc:postgresql://localhost:5432/database_name
DB2
jdbc:db2://localhost:446/dbname
DB2 AS 400
jdbc:as400://hostname/default-schema
Click test button, then the connection information can be verified.
(s)FTP
(s)FTP manages these properties.
Host
(s)FTP Host
Port
(s)FTP Port
FTP Type
File transfer protocol
FTP, sFTP, SCP, FTPs
User
File user
Password
User password
Private key
Private key for sFTP or FTPS connection
Passphrase
Passphrase to access private key
(s)FTP connection can be verified like database.
· Creating a private key
Run this command at the server. If you want a passphrase, enter passphrase otherwise press enter.
$>ssh-keygen -f my-private.key
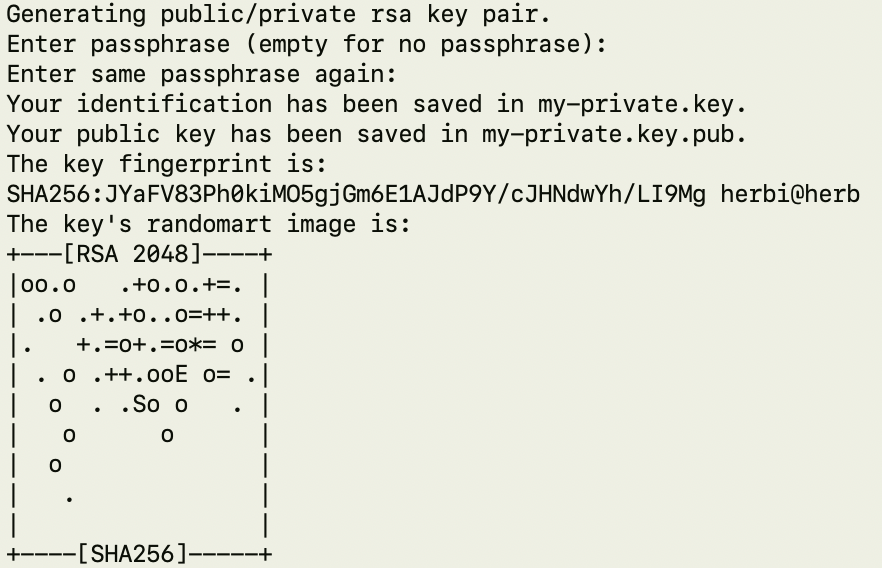
Private and public key pair is generated as my-private.key and my-private.key.pub.
Add public key to the authorized_keys file.
$>cat my-private.key.pub >> ~/.ssh/authorized_keys
Use my-private.key to login sFTP server.
Http(s)
Http manages these properties.
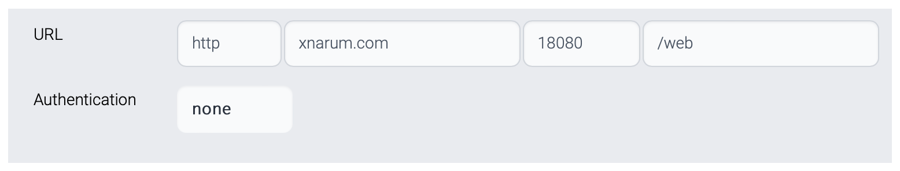
URL
Endpoint of the target Http(s) server
Authenticaiton
None - no authentication
Basic - basic authentication in HTTP header
Digest - Digest authentication
JWT - JWT Token
Custom - Custom authentication with custom class
· Basic authentication
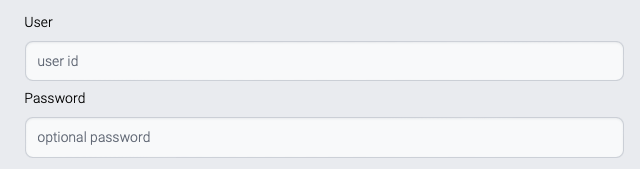
User
User id
Password
Password
Basic authentication adds Authorization header to HTTP header with base64 encoding.
Authorization : Basic a2FpemVuOjEyMzQ1(usename:password)
· Digest authentication
Digest access authentication is one of the agreed-upon methods a web server can use to negotiate credentials, such as username or password, with a user's web browser. This can be used to confirm the identity of a user before sending sensitive information, such as online banking transaction history. It applies a hash function to the username and password before sending them over the network. In contrast, basic access authentication uses the easily reversible Base64 encoding instead of hashing, making it non-secure unless used in conjunction with TLS.
Technically, digest authentication is an application of MD5 cryptographic hashing with usage of nonce values to prevent replay attacks. It uses the HTTP protocol.

· JWT Token
JSON Web Token (JWT) is an open standard (RFC 7519) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed. JWTs can be signed using a secret (with the HMAC algorithm) or a public/private key pair using RSA or ECDSA.
Although JWTs can be encrypted to also provide secrecy between parties, we will focus on signed tokens. Signed tokens can verify the integrity of the claims contained within it, while encrypted tokens hide those claims from other parties. When tokens are signed using public/private key pairs, the signature also certifies that only the party holding the private key is the one that signed it.
(From https://jwt.io/introduction)
JWT token is used to authorize a user after authenticated. JWT Token is generated at the server side with the authentication information sent from the client. If the authentication information is valid, a new JWT Token is generated and returned. This token should be included in all the requests afterwards.
Typically, the server for authentication/authorization has different endpoint.
The token is valid for a finite period. Once the token is expired, a new token should be acquired with the same authentication information.
The token should be included in the HTTP header like this.
Authorization: Bearer <token>
This type of authentication requires these properties.
User
User id
Password
Password
User Field
Field name of the user field
Password Field
Field name of the password field
Content Type
Content type of the authentication request
application/json
application/x-www-form-urlencoded
Authentication URL
Endpoint for the authentication
· Custom authentication
Custom authentication is used to add authentication header to the request. The authentication information can come from a database, a service, or others. Once the authentication information is acquired, that information is added into HTTP header.
This type of authentication requires these properties.
User
User id. Optional
Password
Password. Optional
Class Name
The java class which generates authentication information.
The class should have execute() method and that method should return NameValuePair list.
Socket
Socket manages these properties.
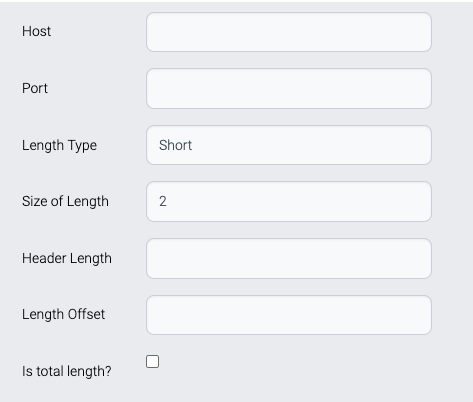
Host
Target host
Port
Listening port of the target server
Length Type
Length field type
· Short - 2 bytes length
· Integer - 4 bytes length
· Character - Stringified length
Short/Integer length is binary data and Character expresses length in character.
ex) 00001200 - Length of the data is 1200 bytes
Size of Length
Size of length field
Short - 2
Integer - 4
Character - Not fixed
Header Length
The length of header data.
Header data contains meta data of the message like followings:
· Length
· Message Type
· Transaction ID
Length Offset
The position of the length field.
Mostly the first few bytes are the length and offset is 0.
Is Total Length?
Does the value of the length field include length field?
· Yes - length field is part of the length.
· No - length field is not part of the length.
Email Server
SMTP system manages these properties.
SMTP Server
SMTP Host. Main and backup, if exists.
Port
SMTP Port. Mostly used ports are these:
25 - non-SSL port
465 - SSL port
Use SSL?
If use ssl, SSL modules are used to connect SMTP server.
User ID
User id of the email server.
Mostly id is the email address of the sender.
Password
Password of the email sender.
IBM MQ
MQ system manages these properties.
Host
MQ Queue manager host
Port
MQ Listener port
Queue Manager
Queue Manager name
Queue Name
Request queue
Channel Name
SVRCONN name
Reply Queue manager
Reply queue manager
Reply Queue Name
Reply queue name
Character Set
Character encoding. Necessary when conversion is required. EBCDIC <-> UTF8
User
User id of the host which MQ is running on
Password
Password
Last updated